‘Hardening’ SoCs For Automotive Market Challenges
, 2014年09月30日
Migrating from mobility into new markets means dealing with new issues such as reliability, security and quality of service.
The semiconductor industry is enamored with the automotive, industrial and medical markets, and many companies are now shifting their focus there. But many mainstream vendors will face challenges entering this market. For those who have traditionally participated in the smart phone or mobility market, I will outline some changes they need to consider to successfully compete in these emerging spaces.
Trend: Shift away from mobility driven by supply and demand
First, a confluence of changes to our industry is causing a shift in the importance of these new markets. Companies such as Texas Instruments, Freescale, Marvell, Intel and Qualcomm are shifting into “automotive” in a big way. But they cut their teeth in mobile phones, so why are they entering markets traditionally dominated by microcontroller vendors? The consolidation and distribution of profits in the mobile phone and tablet arenas has pushed the semiconductor industry to look for new markets that can utilize their existing mobility SoC technology.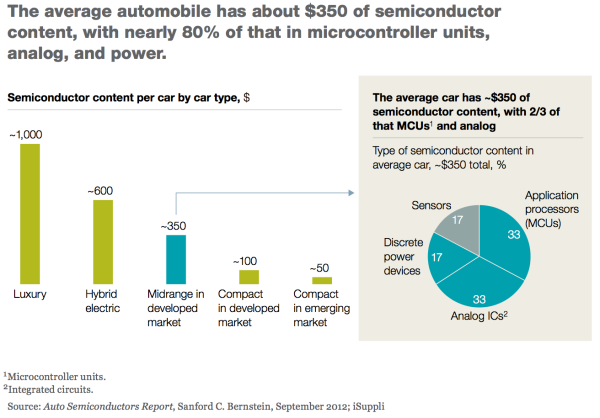
The graph above is from McKinsey’s 2013 report, “Winning Share in Automotive Semiconductors” What are most interesting to new entrants to the automotive semiconductor market are the two green bars on the left: Luxury and hybrid electric cars.
SoCs will require more “hardening”
For large-scale SoCs to replace or augment existing microcontroller functionality, they must be adapted or “hardened” to meet individual market and certification needs.
“Hardening” not only requires enhanced physical and environmental testing requirements. It also necessitates three areas of actual SoC functionality: Reliability, Security and QoS.
1. When things go wrong: Fault tolerance and reliability
Reliability and fault tolerance address unplanned behaviors while a system is in action. For many years, CPU core IP targeted at automotive, medical and industrial markets has incorporated many techniques to increase the reliability of these cores, including:
- ECC and parity bit protection of data;
- Dual-core lockstep (DCLS) – duplicated processing cores shifted in time and space, results compared before accepting as valid;
- Duplicated internal memories – primarily to address soft error rates due to things like cosmic rays, and
- Safety checkers and built-in self tests (BISTs) to check results, and also the checkers.
The Achilles heel to this approach is that only part of the SoC and its data traffic are protected. The only way to ensure there has not been an unanticipated change to data is to enable end-to-end protection of all safety-related communications between initiators and targets on a SoC. This requires protecting the on-chip fabric IP.
2. When hackers attack: Security
Security deals with deliberate human-initiated actions to obtain data from or even control an electronic system.
The methods used to “crack” a target vary in sophistication. The best description and classification I have seen is the one given by Vikas Chandra and Rob Aitken from ARM at their excellent tutorial on Mobile Hardware Security at Hot Chips 2014. Here’s a key graphic from their talk:
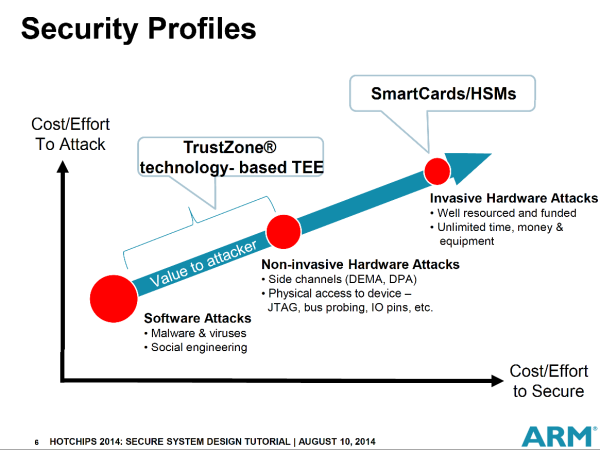
- Software attacks: Viruses and malware are most commonly known, but hackers favor hardware attacks because these have the potential of unlocking all protected data, including keys, in the system.
- Side channel attacks like differential power analysis and differential electromagnetic analysis (DPA/DEMA) measure changes in power consumption or electromagnetic field readings as data is encrypted or decrypted, with the goal of figuring out the content of the encryption keys.
- Physical attacks are meant to “trick” the system into a state that is unintended in the hope that secure content will be revealed openly.
- Invasive attacks are the ones done by large organizations like intelligence agencies and organized criminal gangs, who steal and sell digital content like credit card numbers and pirated videos.
Best practices for SoC security include layering defenses, avoiding single-point vulnerabilities, and enabling quick access reconfiguration or system shutdown when an exploit is discovered.
3. When things get busy: Quality-of-Service (QoS)
In the case of SoCs with many types of transactions occurring simultaneously, it is important that designers can guarantee near real-time / low latency response for some functions at certain times while assuring huge bandwidth for other functions at specific times.
This is especially important for systems that incorporate the human machine interface, like the automobile head unit / infotainment system and the dashboard / instrument panel, such as an advanced driver assistance system (ADAS).
The critical function to having a flexible system that can adapt to changing conditions in the field is to implement SoC hardware than can correctly arbitrate on-chip communication over a fixed number of data paths. This is not a CPU or memory issue but rather a SoC fabric issue. The SoC on-chip communication technology must dynamically adapt to unpredictable changes in priority in near real time.
Semi companies need to act to adapt mobility SoC technology to other markets
The proliferation of mobile and wireless SoC technology into automotive, industrial and medical markets is being driven by the “push” of chip suppliers needing new customers and the “pull” of systems makers wanting the same features and ease of use as we experience with our smartphones.
It is difficult to use off-the-shelf SoCs in these products because these markets require more advanced reliability, security and quality of service. Implementing all three of these SoC features requires an advanced on-chip interconnect fabric. To use their existing technology in these new markets, semiconductor companies must act now by increasing the technological capabilities of their on-chip interconnect fabric IP.